Azure Recovery Services uses certificates to authenticate and encrypt connections to and from the Azure Platform. In the training video -
Configuring Azure Backup In Windows Server 2012 the PKI environment was already setup and configured. This blog entry is the prerequisite to that configuration.
In our lab we have a Domain Controller where Active Directory Certificate Services will be installed and a File Server both using the Windows Server 2012 R2 and Windows Server 2012 Operating Systems. Below is a picture of lab in HYPER-V.
Let's get our PKI installed. On DC-1 we will add a role and select Active Directory Certificate Services.
Next we will take the default selection of a certificate authority and select next.
Once installation is completed our next step is to configure Certificate Authority for Certificate distribution.
When the specify credentials screen appears we will take the defaults and select next.
Select Certificate Authority and select next.
Select Enterprise CA and select next.
Select Root CA and select next.
We will create a new private key and click next.
In the Cryptography for the CA we will select 4096 for the key length SHA256 for the hash algorithm and RSA#Microsoft Software Key Storage Provider for the Cryptographic Provider and click next.
We will use the default for the CA name.
The validity period we will use the length of 3 years.
We will take the database defaults and click next.
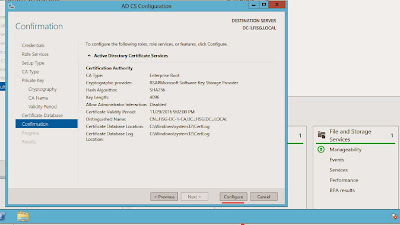
Confirm our configuration and then click configure.
We have successfully configured an Internal PKI environment.
Our Certificate Services is now ready to distribute certificates on the network and to Azure!
Next we will head to our File Server and select run then enter mmc for the Microsoft Management Console.
In the console we will select file then Add-Remove Snap-in.
In the Snap-in select Certificates then the add button.
Select the Computer Account then click next.
Leave the default selection for the Local Computer then select Finish.
Note that the Certificates on the Local Computer is selected for management. Click ok.
Expand Certificates, then Personal and then Certificates.
Right click an empty spot in the right pane for the menu to appear. Select All tasks then Request a New Certificate.
The Enrollment wizard will kick off the click next.
Select computer then Enroll.
The certificate request for enrollment is successful! Click Finish to close out.
Our next step is to export the certificate. Make sure that the certificate you are exporting is the Client Authenticated one. Select your certificate right click, select all task then export.
Do not export the private key as it is not needed for Azure Recovery Services. Click next.
We will take the default of the DER encoded binary X.509 cert.
I will place the certificate on the desktop for easy access.
The export of our certificate is successful!
You now have a certificate for your Azure Recovery Services Vault in the Azure platform!